SSH backdoor via liblzma / xz
A fascinating sequence of events around an SSH backdoor that had been slipped into XZ utils by someone who had been contributing to the project for 2 years, gaining trust. It was discovered by Andres Freund after he noticed an extra 500ms of latency on his SSH connections and he did some digging. Incredible detective work here.

The impact of this could have been massive, and the interesting part is how the change made it into the library and was in the process of being included in many major Linux distributions.

A pull request that was part of the attempt to hide the backdoor:


The author of the backdoor has been now subsequently investigated by many across the internet and have found a lot of interesting information about their patterns of work.
Below is a good summary of the timeline of events.


There's strong speculation that this was a state actor, and had this supply chain attack been successfully pulled off, the impact could have been pretty significant.
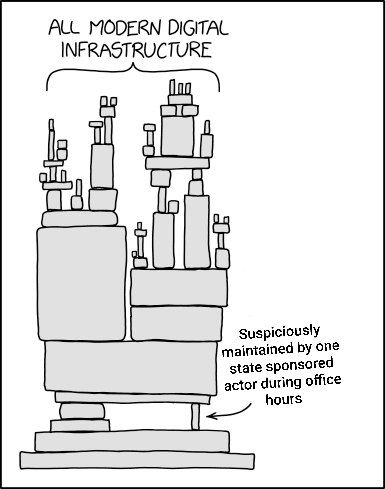
Another important point made by Rob Mensching:
The original maintainer burns out, and only the attacker offers to help (so the attacker inherits the trust of the project built by the maintainer).

Overall, we seem to have got pretty lucky here - though there's some concern over a possible compromise of libarchive too due to the author of this backdoor having contributed code there.
Hopefully it serves as a sufficient wake-up call for the OSS community to improve processes to fend off these attacks, and ideally, the trillion dollar corporations that benefit from much of this free and open source software could contribute back more to help much more than they currently do.

Member discussion